林超(2017级) <更新时间 2022-06-07 14:33>
林超,男,福建平和人,生于1991,性格乐观,凡事尽心,结果随缘。 如今正在科研路上积累沉淀成长! 学习使我快乐,科研让我成长,运动给我健康!
教育及工作经历
2017年9月至今,武汉大学国家网络安全学院,攻读博士学位
2017年2月 – 2017年5月 台湾清华大学, 访学
2014年9月-2017年7月,福建师范大学数学与计算机科学学院,硕士
2013年9月-2014年7月,甘肃省定西市漳县城关中学,支教
2009年9月-2013年7月,福建师范大学数学与计算机科学学院,本科
学术成果
专栏
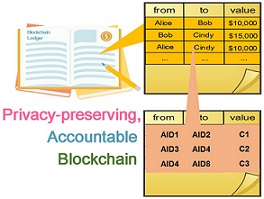
Bibliography on Privacy-preserving and Accountable Blockchain
Maintained by
Chao Lin, Email: linchao91@whu.edu.cn
Supported by
Professor Debiao He, Email: hedebiao@163.com
School of Cyber Science and Engineering, Wuhan University, Wuhan, China

As a new decentralized computing paradigm, the blockchain demonstrates the great potential for large-scale collaboration in a self-organizing mode, provides a new approach to solve the consistency problems in distribute networks, and has attracted extensive attention from academia and industry. However, the openness of blockchain system and the uncontrollability of its computing environment pose a great threat to users’ sensitive data and personal privacy. The exiting solutions have some drawbacks, such as it is difficult to balance privacy protection and legal supervision, and lacking protection for users’ keys, which leads to frequent accidents such as money laundering, extortion, loss of digital assets, and so forth. Thus, it is essential to research the key cryptographic technologies for privacy protection and regulation in blockchain systems.
We try our best to maintain a complete list of bibliography on privacy-preserving and accountable blockchain on the internet, and hope this can be helpful for researchers in the relevant field.
Generally, we are including literatures in English, which are published in conference proceedings, journals, and some unpublished technical reports or dissertations. We would appreciate knowing of any errors in this list, as well as any literatures that should be added. Please e-mail to us.

Call for Papers
· ACM Transactions on Internet of Technology (TOIT), Special Issue on: "Decentralized Blockchain Applications and Infrastructures for Next Generation Cyber-Physical Systems" [HTML] [Manuscript Due, November 30, 2019]
· Computers & Security, Special Issue on: "Blockchain and Cryptocurrency" [HTML] [Manuscript Due, November 30, 2018]
Bibliography on Privacy-preserving and Accountable Blockchain
2019
· [CZDZW19] C. Cai, Y. Zheng, Y. Du, Z. Qin, and C. Wang. Towards Private, Robust, and Verifiable Crowdsensing Systems via Public Blockchains. IEEE Transactions on Dependable and Secure Computing, 2019. DOI: 10.1109/TDSC.2019.2941481
· [ZWXGQZ19] H. Zheng, Q. Wu, J. Xie, Z. Guan, B. Qin, and Z. Gu. An Organization-friendly Blockchain System. Computers & Security, 2019. DOI: 10.1016/j.cose.2019.101598
· [LYSYAL19] Y. Li, G. Yang, W. Susilo, Y. Yu, M. H. Au, and D. Liu. Traceable Monero: Anonymous Cryptocurrency with Enhanced Accountability. IEEE Transactions on Dependable and Secure Computing, 2019. DOI: 10.1109/TDSC.2019.2910058
· [RZ19] A. Rondelet, and M. Zajac. ZETH: On Integrating Zerocash on Ethereum. arXiv preprint arXiv:1904.00905, 2019.
· [BAZB19] B. Bünz, S. Agrawal, M. Zamani, and D. Boneh. Zether: Towards Privacy in a Smart Contract World. IACR Cryptology ePrint Archive, 2019.
· [CC19] C. D. Clack, and N. T. Courtois. Distributed Ledger Privacy: Ring Signatures, Mobius and CryptoNote. arXiv preprint arXiv:1902.02609, 2019.
· [FOS19] G. Fuchsbauer, M. Orrù, and Y. Seurin. Aggregate Cash Systems: A Cryptographic Investigation of Mimblewimble. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 657-689, 2019.
· [WFWZ19] Y. Wu, H. Fan, X. Wang, and G. Zou. A Regulated Digital Currency. Science China Information Sciences, vol. 62, no. 3, pp. 32109, 2019.
· [LSYYDLG19] Y. Li, W. Susilo, G. Yang, Y. Yu, X. Du, D. Liu, and N. Guizani. Toward Privacy and Regulation in Blockchain-based Cryptocurrencies. IEEE Network, 2019. DOI: 10.1109/MNET.2019.1800271
· [YAXY19]R. Yang, M. H. Au, Q. Xu, and Z. Yu. Decentralized blacklistable anonymous credentials with reputation. Computers & Security, vol. 85, pp. 353-371, 2019.
· [LWYLZHLXD19] M. Li, J. Weng, A. Yang, W. Lu, Y. Zhang, L. Hou, J. Liu, Y. Xiang, and R. H. Deng. CrowdBC: A blockchain-based decentralized framework for crowdsourcing. IEEE Transactions on Parallel and Distributed Systems, vol. 30, no.6, pp. 1251-1266, 2019.
· [YY19] H. Yang, and B. Yang. A blockchain-based approach to the secure sharing of healthcare data. In Proceedings of the Norwegian Information Security Conference, 2017.
· [MLBKY19] A. Manzoor, M. Liyanage, A. Braeke, S. S. Kanhere, and M. Ylianttila. Blockchain based proxy re-encryption scheme for secure IoT data sharing. In Proceedings of IEEE International Conference on Blockchain and Cryptocurrency, pp. 99-103, 2019.
· [ABPH19] M. A. Azad, S. Bag, S. Parkinson, and F. Hao. TrustVote: privacy-preserving node ranking in vehicular networks. IEEE Internet of Things Journal, vol. 6, no. 4, pp. 5878 - 5891, 2019.
· [YCMMB19] Y. Yao, X. Chang, J. Mišić, V. B. Mišić, and L. Li. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet of Things Journal, vol. 6, no. 2, pp. 3775-3784, 2019.
· [WLIL19] J. Wan, J. Li, M. Imran, and D. Li. A blockchain-based solution for enhancing security and privacy in smart factory. IEEE Transactions on Industrial Informatics, vol. 15, no. 6, pp. 3652 - 3660, 2019.
· [ZLLACCT19] L. Zhang, M. Luo, J. Li, M. H. Au, K. K. R. Choo, T. Chen, and S. Tian. Blockchain based secure data sharing system for Internet of vehicles: A position paper. Vehicular Communications, vol. 16, pp. 85-93, 2019.
· [GWZXZ19] K. Gai, Y. Wu, L. Zhu, L. Xu, and Y. Zhang. Permissioned Blockchain and Edge Computing Empowered Privacy-preserving Smart Grid Networks. IEEE Internet of Things Journal, vol. 6, no. 5, pp. 7992 - 8004, 2019.
· [ZJGGW19] D. Zheng, C. Jing, R. Guo, S. Gao, and L. Wang. A Traceable Blockchain-Based Access Authentication System With Privacy Preservation in VANETs, IEEE Access, vol. 7, pp. 117716-117726, 2019.
· [ZWWLL19] Y. Zhang, J. Weng, J. Weng, M. Li, and W. Luo. Onionchain: Towards Balancing Privacy and Traceability of Blockchain-Based Applications. arXiv preprint arXiv:1909.03367, 2019.
· [ACCDET19] E. Androulaki, J. Camenisch, A. De Caro, M. Dubovitskaya, K. Elkhiyaoui, and B. Tackmann. Privacy-preserving auditable token payments in a permissioned blockchain system. arXiv preprint, 2019.
· [ZLLLG19] Y. Zhang, Y. Long, Z. Liu, Z. Liu, and D. Gu. Z-channel: Scalable and efficient scheme in Zerocash. Computers & Security, 2019. DOI: 10.1016/j.cose.2019.05.012.
2018
· [FMMO18] P. Fauzi, S. Meiklejohn, R. Mercer, and C. Orlandi. QuisQuis: A New Design for Anonymous Cryptocurrencies. IACR Cryptology ePrint Archive, 2018.
· [YXCZX18] R. Yuan, Y. B. Xia, H. B. Chen, B. Y. Zang, and J. Xie. Shadoweth: Private smart contract on public blockchain. Journal of Computer Science and Technology, vol. 33, no. 3, pp. 542-556, 2018.
· [ZZSZLY18] B. K. Zheng, L. H. Zhu, M. Shen, F. Gao, C. Zhang, Y. D. Li, and J. Yang. Scalable and privacy-preserving data sharing based on blockchain. Journal of Computer Science and Technology, vol. 33, no. 3, pp. 557-567, 2018.
· [NVV18] N. Narula, W. Vasquez, and M. Virza. zkLedger: Privacy-preserving Auditing for Distributed Ledgers. In Proceedings of 15th USENIX Symposium on Networked Systems Design and Implementation, pp. 65-80, 2018.
· [LTW18] Y. Lu, Q. Tang, and G. Wang. Zebralancer: Private and Anonymous Crowdsourcing System Atop Open Blockchain. In Proceedings of IEEE 38th International Conference on Distributed Computing Systems, pp. 853-865, 2018.
· [GGM18] C. Garman, M. Green, and I. Miers. Accountable Privacy for Decentralized Anonymous Payments. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 81-98, 2018.
· [FHZKK18] Q. Feng, D. He, S. Zeadally, M. K. Khan, and N. Kumar. A Survey on Privacy Protection in Blockchain System. Journal of Network and Computer Applications, 2018. DOI: 10.1016/j.jnca.2018.10.020
· [LCCM18] B. Lian, G. Chen, J. Cui, and M. Ma. Compact E-Cash with Efficient Coin-Tracing. IEEE Transactions on Dependable and Secure Computing, 2018. DOI: 10.1109/TDSC.2018.2882507
· [HCWWLR18] S. Hu, C. Cai, Q. Wang, C. Wang, X. Luo, and K. Ren. Searching an encrypted cloud meets blockchain: A decentralized, reliable and fair realization. In Proceedings of IEEE INFOCOM 2018-IEEE Conference on Computer Communications, pp. 792-800, 2018.
· [CYYHJD18] J. Chen, S. Yao, Q. Yuan, K. He, S. Ji, and R. Du. CertChain: Public and efficient certificate audit based on blockchain for TLS connections. In Proceedings of IEEE INFOCOM 2018-IEEE Conference on Computer Communications, pp. 2060-2068, 2018.
· [YCX18] C. Yang, X. Chen, and Y. Xiang. Blockchain-based publicly verifiable data deletion scheme for cloud storage. Journal of Network and Computer Applications, vol. 103, pp. 185-193, 2018.
· [HWLLLFL18] S. He, Q. Wu, X. Luo, Z. Liang, D. Li, H. Feng, and Y. Li. A social-network-based cryptocurrency wallet-management scheme. IEEE Access, vol. 6, pp. 7654-7663, 2018.
· [LLCQWZZ18] L. Li, J. Liu, L. Cheng, S. Qiu, W. Wang, X. Zhang, and Z. Zhang. Creditcoin: A privacy-preserving blockchain-based incentive announcement network for communications of smart vehicles. IEEE Transactions on Intelligent Transportation Systems, vol. 19, no. 7, pp. 2204-2220, 2018.
· [FRHP18] E. C. Ferrer, O. Rudovic, T. Hardjono, and A. Pentland. Robochain: A secure data-sharing framework for human-robot interaction. arXiv preprint arXiv:1802.04480, 2018.
· BDN18] D. Boneh, M. Drijvers, and G. Neven. Compact multi-signatures for smaller blockchains. In Proceedings of International Conference on the Theory and Application of Cryptology and Information Security, pp. 435-464, 2018.
· [LM18] T. Le, and M. W. Mutka. CapChain: A privacy preserving access control framework based on blockchain for pervasive environments. In Proceedings of IEEE International Conference on Smart Computing, pp. 57-64, 2018.
· [KYMM18] G. Kappos, H. Yousaf, M. Maller, and S. Meiklejohn. An empirical analysis of anonymity in zcash. In Proceedings of 27th USENIX Security Symposium, pp. 463-477, 2018.
· [FPSGW18] J. Frankle, S. Park, D. Shaar, S. Goldwasser, and D. Weitzner. Practical accountability of secret processes. In Proceedings of 27th USENIX Security Symposium, pp. 657-674, 2018.
· [KA18] K. Kluczniak, and M. H. Au. Fine-Tuning Decentralized Anonymous Payment Systems based on Arguments for Arithmetic Circuit Satisfiability. IACR Cryptology ePrint Archive, 2018.
· [LLWQL18] Z. Lu, W. Liu, Q. Wang, G. Qu, and Z. Liu. A privacy-preserving trust model based on blockchain for vanets. IEEE Access, vol. 6, pp. 45655-45664, 2018.
· [DCFZ18] T. Duong, A. Chepurnoy, L. Fan, and H. S. Zhou. Twinscoin: A cryptocurrency via proof-of-work and proof-of-stake. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, pp. 1-13, 2018.
· [HZ18] K. Hu, and Z. Zhang. Fast Lottery-Based Micropayments for Decentralized Currencies. In Australasian Conference on Information Security and Privacy, pp. 669-686, 2018.
2017
· [NYSS17] K. Naganuma, M. Yoshino, H. Sato, and T. Suzuki. Auditable zerocoin. In Proceedings of IEEE European Symposium on Security and Privacy Workshops, pp. 59-63, 2017.
· [CGLMMM17] A. Chiesa, M. Green, J. Liu, P. Miao, I. Miers, and P. Mishra. Decentralized Anonymous Micropayments. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 609-642, 2017.
· [SALY17] S. F. Sun, M. H. Au, J. K. Liu, and T. H. Yuen. RingCT 2.0: A Compact Accumulator-based (Linkable Ring Signature) Protocol for Blockchain Cryptocurrency Monero. In Proceedings of European Symposium on Research in Computer Security, pp. 456-474, 2017.
· [WGZX17] Z. Wan, Z. Guan, F. Zhuo, and H. Xian. BKI: Towards accountable and decentralized public-key infrastructure with blockchain. In Proceedings of International Conference on Security and Privacy in Communication Systems, pp. 644-658, 2017.
· [AZV17] M. Apostolaki, A. Zohar, and L. Vanbever. Hijacking bitcoin: Routing attacks on cryptocurrencies. In Proceedings of IEEE Symposium on Security and Privacy, pp. 375-392, 2017.
· [MDB17] A. Moinet, B. Darties, and J. L. Baril. Blockchain based trust & authentication for decentralized sensor networks. arXiv preprint arXiv:1706.01730, 2017.
· [LSTKKN17] X. Liang, S. Shetty, D. Tosh, C. Kamhoua, K. Kwiat, and L. Njilla. Provchain: A blockchain-based data provenance architecture in cloud environment with enhanced privacy and availability. In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, pp. 468-477, 2017.
· [KMHKB17] H. Kopp, D. Mödinger, F. Hauck, F. Kargl, and C. Bösch. Design of a privacy-preserving decentralized file storage with financial incentives. In Proceedings of IEEE European Symposium on Security and Privacy Workshops, pp. 14-22, 2017.
· [CGLMMM17] A. Chiesa, M. Green, J. Liu, P. Miao, I. Miers, and P. Mishra. Decentralized anonymous micropayments. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 609-642, 2017.
· [SRKKN17] S. Shetty, V. Red, C. Kamhoua, K. Kwiat, and L. Njilla. Data provenance assurance in the cloud using blockchain. In Proceedings of SPIE 10206, Disruptive Technologies in Sensors and Sensor Systems, 102060I, 2017.
· [GM17] M. Green, and I. Miers. Bolt: Anonymous payment channels for decentralized currencies. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 473-489, 2017.
· [ACCG17] D. Augot, H. Chabanne, O. Clémot, and W. George. Transforming face-to-face identity proofing into anonymous digital identity using the bitcoin blockchain. In Proceedings of 15th Annual Conference on Privacy, Security and Trust, pp. 25-2509, 2017.
· [CGGN17] M. Campanelli, R. Gennaro, S. Goldfeder, and L. Nizzardo. Zero-knowledge contingent payments revisited: Attacks and payments for services. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, pp. 229-243, 2017.
· [XCGLS17] L. Xu, L. Chen, Z. Gao, Y. Lu, and W. Shi. CoC: secure supply chain management system based on public ledger. In Proceedings of 26th International Conference on Computer Communication and Networks, pp. 1-6, 2017.
· [HFC17] S. H. Hashemi, F. Faghri, and R. H. Campbell. Decentralized user-centric access control using pubsub over blockchain. arXiv preprint arXiv:1710.00110, 2017.
· [LOE17] H. Lycklama à Nijeholt, J. Oudejans, and Z. Erkin. Decreg: A framework for preventing double-financing using blockchain technology. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, pp. 29-34, 2017.
· [PSRK17] C. Patsonakis, K. Samari, M. Roussopoulos, and A. Kiayias. Towards a smart contract-based, decentralized, public-key infrastructure. In Proceedings of International Conference on Cryptology and Network Security, pp. 299-321, 2017.
· [KFTS17] A. Kumar, C. Fischer, S. Tople, and P. Saxena. A traceability analysis of monero’s blockchain. In Proceedings of European Symposium on Research in Computer Security, pp. 153-173, 2017.
· [FV17] G. Fanti, and P. Viswanath. Anonymity properties of the Bitcoin P2P network. arXiv preprint arXiv:1703.08761, 2017.
· [XSSAZ17] Q. Xia, E. Sifah, A. Smahi, S. Amofa, and X. Zhang. BBDS: Blockchain-based data sharing for electronic medical records in cloud environments. Information, vol. 8, no. 2, pp. 44, 2017.
· [CZJKJS17] E. Cecchetti, , F. Zhang Y. Ji, A. Kosba, A. Juels, and E. Shi. Solidus: Confidential distributed ledger transactions via PVORM. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 701-717, 2017.
2016
· [AS16] N. Z. Aitzhan, and D. Svetinovic. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 5, pp. 840-852, 2016.
2015
· [N15] S. Noether. Ring SIgnature Confidential Transactions for Monero. IACR Cryptology ePrint Archive, 1098, 2015.
· [ZGHIW15] J. H. Ziegeldorf, F. Grossmann, M. Henze, N. Inden, and K. Wehrle. Coinparty: Secure Multi-party Mixing of Bitcoins. In Proceedings of the 5th ACM Conference on Data and Application Security and Privacy, pp. 75-86, 2015.
· [VR15] L. Valenta, and B. Rowan. Blindcoin: Blinded, Accountable Mixes for Bitcoin. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 112-126, 2015.
2014
· [SCGMTV14] E. B. Sasson, A. Chiesa, C. Garman, M. Green, I. Miers, E. Tromer, and M. Virza. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of IEEE Symposium on Security and Privacy, pp. 459-474, 2014.
· [BNMCKF14] J. Bonneau, A. Narayanan, A. Miller, J. Clark, J. A. Kroll, and E. W. Felten. Mixcoin: Anonymity for Bitcoin with accountable mixes. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 486-504, 2014.
· [GCKG14] A. Gervais, S. Capkun, G. O. Karame, and D. Gruber. On the privacy provisions of bloom filters in lightweight bitcoin clients. In Proceedings of the 30th Annual Computer Security Applications Conference, pp. 326-335, 2014.
2013
· [MGR13] I. Miers, C. Garman, M. Green, and A. D. Rubin. Zerocoin: Anonymous Distributed E-cash from Bitcoin. In Proceedings of IEEE Symposium on Security and Privacy, pp. 397-411, 2013.
2017年9月至今,武汉大学国家网络安全学院,攻读博士学位
2017年2月 – 2017年5月 台湾清华大学, 访学
2014年9月-2017年7月,福建师范大学数学与计算机科学学院,硕士
2013年9月-2014年7月,甘肃省定西市漳县城关中学,支教
2009年9月-2013年7月,福建师范大学数学与计算机科学学院,本科
学术成果
[1] Chao Lin, Debiao He, Xinyi Huang, Kim-Kwang Raymond Choo. Secure and Privacy-preserving Smart Contract-based Solution for Access Control in IoT. Newsletter (2018).
[2] Chao Lin, Debiao He, Xinyi Huang, Muhammad Khurram Khan, and Kim-Kwang Raymond Choo. A New Transitively Closed
Undirected Graph Authentication Scheme for Blockchain-based Identity Management Systems. IEEE ACCESS 6: 28203-28212 (2018).
[3] Chao Lin, Debiao He, Xinyi Huang, Kim-Kwang Raymond Choo, Athanasios V. Vasilakos. BSeIn: A blockchain-based
secure mutual authentication with fine-grained access control system for industry 4.0. Journal of Network and Computer Applications 116: 42-52 (2018).
[4] Chao Lin, Debiao He, Neeraj Kumar, Kim-Kwang Raymond Choo, Alexey Vinel, Xinyi Huang: Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Communications Magazine 56(1): 64-69 (2018).
[5] Chao Lin, Wei Wu, Xinyi Huang, Li Xu. A New Universal Designated Verifier Transitive Signature Scheme for Big Graph Data [J]. Journal of Computer and System Sciences 83(1): 73-83, 2017.
[6] Chao Lin, Fei Zhu, Wei Wu, Kaitai Liang, Kim-Kwang Raymond Choo. A New Transitive Signature Scheme [C]. Lecture Notes in Computer Science, 9955. NSS 2016: 156-167.
其他成果
[1] 2018. 荣获博士研究生创新奖学金一等奖,博士研究生学业奖学金一等奖,国家网络安全学院博士论坛一等奖,优秀研究生
[2] Chao Lin, Debiao He, Xinyi Huang, Muhammad Khurram Khan, and Kim-Kwang Raymond Choo. A New Transitively Closed
Undirected Graph Authentication Scheme for Blockchain-based Identity Management Systems. IEEE ACCESS 6: 28203-28212 (2018).
[3] Chao Lin, Debiao He, Xinyi Huang, Kim-Kwang Raymond Choo, Athanasios V. Vasilakos. BSeIn: A blockchain-based
secure mutual authentication with fine-grained access control system for industry 4.0. Journal of Network and Computer Applications 116: 42-52 (2018).
[4] Chao Lin, Debiao He, Neeraj Kumar, Kim-Kwang Raymond Choo, Alexey Vinel, Xinyi Huang: Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Communications Magazine 56(1): 64-69 (2018).
[5] Chao Lin, Wei Wu, Xinyi Huang, Li Xu. A New Universal Designated Verifier Transitive Signature Scheme for Big Graph Data [J]. Journal of Computer and System Sciences 83(1): 73-83, 2017.
[6] Chao Lin, Fei Zhu, Wei Wu, Kaitai Liang, Kim-Kwang Raymond Choo. A New Transitive Signature Scheme [C]. Lecture Notes in Computer Science, 9955. NSS 2016: 156-167.
[7] Chao Lin, Debiao He, Xinyi Huang, Xiang Xie, Kim-Kwang Raymond Choo. Blockchain-based system for secure outsourcing of bilinear pairings. Information Sciences (2018). DOI:10.1016/j.ins.2018.12.043.
其他成果
[1] 2018. 荣获博士研究生创新奖学金一等奖,博士研究生学业奖学金一等奖,国家网络安全学院博士论坛一等奖,优秀研究生
专栏
Bibliography on Privacy-preserving and Accountable Blockchain

Maintained by
Chao Lin, Email: linchao91@whu.edu.cn
Supported by
Professor Debiao He, Email: hedebiao@163.com
School of Cyber Science and Engineering, Wuhan University, Wuhan, China

As a new decentralized computing paradigm, the blockchain demonstrates the great potential for large-scale collaboration in a self-organizing mode, provides a new approach to solve the consistency problems in distribute networks, and has attracted extensive attention from academia and industry. However, the openness of blockchain system and the uncontrollability of its computing environment pose a great threat to users’ sensitive data and personal privacy. The exiting solutions have some drawbacks, such as it is difficult to balance privacy protection and legal supervision, and lacking protection for users’ keys, which leads to frequent accidents such as money laundering, extortion, loss of digital assets, and so forth. Thus, it is essential to research the key cryptographic technologies for privacy protection and regulation in blockchain systems.
We try our best to maintain a complete list of bibliography on privacy-preserving and accountable blockchain on the internet, and hope this can be helpful for researchers in the relevant field.
Generally, we are including literatures in English, which are published in conference proceedings, journals, and some unpublished technical reports or dissertations. We would appreciate knowing of any errors in this list, as well as any literatures that should be added. Please e-mail to us.

Call for Papers
· ACM Transactions on Internet of Technology (TOIT), Special Issue on: "Decentralized Blockchain Applications and Infrastructures for Next Generation Cyber-Physical Systems" [HTML] [Manuscript Due, November 30, 2019]
· Computers & Security, Special Issue on: "Blockchain and Cryptocurrency" [HTML] [Manuscript Due, November 30, 2018]
Bibliography on Privacy-preserving and Accountable Blockchain
2019
· [CZDZW19] C. Cai, Y. Zheng, Y. Du, Z. Qin, and C. Wang. Towards Private, Robust, and Verifiable Crowdsensing Systems via Public Blockchains. IEEE Transactions on Dependable and Secure Computing, 2019. DOI: 10.1109/TDSC.2019.2941481
· [ZWXGQZ19] H. Zheng, Q. Wu, J. Xie, Z. Guan, B. Qin, and Z. Gu. An Organization-friendly Blockchain System. Computers & Security, 2019. DOI: 10.1016/j.cose.2019.101598
· [LYSYAL19] Y. Li, G. Yang, W. Susilo, Y. Yu, M. H. Au, and D. Liu. Traceable Monero: Anonymous Cryptocurrency with Enhanced Accountability. IEEE Transactions on Dependable and Secure Computing, 2019. DOI: 10.1109/TDSC.2019.2910058
· [RZ19] A. Rondelet, and M. Zajac. ZETH: On Integrating Zerocash on Ethereum. arXiv preprint arXiv:1904.00905, 2019.
· [BAZB19] B. Bünz, S. Agrawal, M. Zamani, and D. Boneh. Zether: Towards Privacy in a Smart Contract World. IACR Cryptology ePrint Archive, 2019.
· [CC19] C. D. Clack, and N. T. Courtois. Distributed Ledger Privacy: Ring Signatures, Mobius and CryptoNote. arXiv preprint arXiv:1902.02609, 2019.
· [FOS19] G. Fuchsbauer, M. Orrù, and Y. Seurin. Aggregate Cash Systems: A Cryptographic Investigation of Mimblewimble. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 657-689, 2019.
· [WFWZ19] Y. Wu, H. Fan, X. Wang, and G. Zou. A Regulated Digital Currency. Science China Information Sciences, vol. 62, no. 3, pp. 32109, 2019.
· [LSYYDLG19] Y. Li, W. Susilo, G. Yang, Y. Yu, X. Du, D. Liu, and N. Guizani. Toward Privacy and Regulation in Blockchain-based Cryptocurrencies. IEEE Network, 2019. DOI: 10.1109/MNET.2019.1800271
· [YAXY19]R. Yang, M. H. Au, Q. Xu, and Z. Yu. Decentralized blacklistable anonymous credentials with reputation. Computers & Security, vol. 85, pp. 353-371, 2019.
· [LWYLZHLXD19] M. Li, J. Weng, A. Yang, W. Lu, Y. Zhang, L. Hou, J. Liu, Y. Xiang, and R. H. Deng. CrowdBC: A blockchain-based decentralized framework for crowdsourcing. IEEE Transactions on Parallel and Distributed Systems, vol. 30, no.6, pp. 1251-1266, 2019.
· [YY19] H. Yang, and B. Yang. A blockchain-based approach to the secure sharing of healthcare data. In Proceedings of the Norwegian Information Security Conference, 2017.
· [MLBKY19] A. Manzoor, M. Liyanage, A. Braeke, S. S. Kanhere, and M. Ylianttila. Blockchain based proxy re-encryption scheme for secure IoT data sharing. In Proceedings of IEEE International Conference on Blockchain and Cryptocurrency, pp. 99-103, 2019.
· [ABPH19] M. A. Azad, S. Bag, S. Parkinson, and F. Hao. TrustVote: privacy-preserving node ranking in vehicular networks. IEEE Internet of Things Journal, vol. 6, no. 4, pp. 5878 - 5891, 2019.
· [YCMMB19] Y. Yao, X. Chang, J. Mišić, V. B. Mišić, and L. Li. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet of Things Journal, vol. 6, no. 2, pp. 3775-3784, 2019.
· [WLIL19] J. Wan, J. Li, M. Imran, and D. Li. A blockchain-based solution for enhancing security and privacy in smart factory. IEEE Transactions on Industrial Informatics, vol. 15, no. 6, pp. 3652 - 3660, 2019.
· [ZLLACCT19] L. Zhang, M. Luo, J. Li, M. H. Au, K. K. R. Choo, T. Chen, and S. Tian. Blockchain based secure data sharing system for Internet of vehicles: A position paper. Vehicular Communications, vol. 16, pp. 85-93, 2019.
· [GWZXZ19] K. Gai, Y. Wu, L. Zhu, L. Xu, and Y. Zhang. Permissioned Blockchain and Edge Computing Empowered Privacy-preserving Smart Grid Networks. IEEE Internet of Things Journal, vol. 6, no. 5, pp. 7992 - 8004, 2019.
· [ZJGGW19] D. Zheng, C. Jing, R. Guo, S. Gao, and L. Wang. A Traceable Blockchain-Based Access Authentication System With Privacy Preservation in VANETs, IEEE Access, vol. 7, pp. 117716-117726, 2019.
· [ZWWLL19] Y. Zhang, J. Weng, J. Weng, M. Li, and W. Luo. Onionchain: Towards Balancing Privacy and Traceability of Blockchain-Based Applications. arXiv preprint arXiv:1909.03367, 2019.
· [ACCDET19] E. Androulaki, J. Camenisch, A. De Caro, M. Dubovitskaya, K. Elkhiyaoui, and B. Tackmann. Privacy-preserving auditable token payments in a permissioned blockchain system. arXiv preprint, 2019.
· [ZLLLG19] Y. Zhang, Y. Long, Z. Liu, Z. Liu, and D. Gu. Z-channel: Scalable and efficient scheme in Zerocash. Computers & Security, 2019. DOI: 10.1016/j.cose.2019.05.012.
2018
· [FMMO18] P. Fauzi, S. Meiklejohn, R. Mercer, and C. Orlandi. QuisQuis: A New Design for Anonymous Cryptocurrencies. IACR Cryptology ePrint Archive, 2018.
· [YXCZX18] R. Yuan, Y. B. Xia, H. B. Chen, B. Y. Zang, and J. Xie. Shadoweth: Private smart contract on public blockchain. Journal of Computer Science and Technology, vol. 33, no. 3, pp. 542-556, 2018.
· [ZZSZLY18] B. K. Zheng, L. H. Zhu, M. Shen, F. Gao, C. Zhang, Y. D. Li, and J. Yang. Scalable and privacy-preserving data sharing based on blockchain. Journal of Computer Science and Technology, vol. 33, no. 3, pp. 557-567, 2018.
· [NVV18] N. Narula, W. Vasquez, and M. Virza. zkLedger: Privacy-preserving Auditing for Distributed Ledgers. In Proceedings of 15th USENIX Symposium on Networked Systems Design and Implementation, pp. 65-80, 2018.
· [LTW18] Y. Lu, Q. Tang, and G. Wang. Zebralancer: Private and Anonymous Crowdsourcing System Atop Open Blockchain. In Proceedings of IEEE 38th International Conference on Distributed Computing Systems, pp. 853-865, 2018.
· [GGM18] C. Garman, M. Green, and I. Miers. Accountable Privacy for Decentralized Anonymous Payments. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 81-98, 2018.
· [FHZKK18] Q. Feng, D. He, S. Zeadally, M. K. Khan, and N. Kumar. A Survey on Privacy Protection in Blockchain System. Journal of Network and Computer Applications, 2018. DOI: 10.1016/j.jnca.2018.10.020
· [LCCM18] B. Lian, G. Chen, J. Cui, and M. Ma. Compact E-Cash with Efficient Coin-Tracing. IEEE Transactions on Dependable and Secure Computing, 2018. DOI: 10.1109/TDSC.2018.2882507
· [HCWWLR18] S. Hu, C. Cai, Q. Wang, C. Wang, X. Luo, and K. Ren. Searching an encrypted cloud meets blockchain: A decentralized, reliable and fair realization. In Proceedings of IEEE INFOCOM 2018-IEEE Conference on Computer Communications, pp. 792-800, 2018.
· [CYYHJD18] J. Chen, S. Yao, Q. Yuan, K. He, S. Ji, and R. Du. CertChain: Public and efficient certificate audit based on blockchain for TLS connections. In Proceedings of IEEE INFOCOM 2018-IEEE Conference on Computer Communications, pp. 2060-2068, 2018.
· [YCX18] C. Yang, X. Chen, and Y. Xiang. Blockchain-based publicly verifiable data deletion scheme for cloud storage. Journal of Network and Computer Applications, vol. 103, pp. 185-193, 2018.
· [HWLLLFL18] S. He, Q. Wu, X. Luo, Z. Liang, D. Li, H. Feng, and Y. Li. A social-network-based cryptocurrency wallet-management scheme. IEEE Access, vol. 6, pp. 7654-7663, 2018.
· [LLCQWZZ18] L. Li, J. Liu, L. Cheng, S. Qiu, W. Wang, X. Zhang, and Z. Zhang. Creditcoin: A privacy-preserving blockchain-based incentive announcement network for communications of smart vehicles. IEEE Transactions on Intelligent Transportation Systems, vol. 19, no. 7, pp. 2204-2220, 2018.
· [FRHP18] E. C. Ferrer, O. Rudovic, T. Hardjono, and A. Pentland. Robochain: A secure data-sharing framework for human-robot interaction. arXiv preprint arXiv:1802.04480, 2018.
· BDN18] D. Boneh, M. Drijvers, and G. Neven. Compact multi-signatures for smaller blockchains. In Proceedings of International Conference on the Theory and Application of Cryptology and Information Security, pp. 435-464, 2018.
· [LM18] T. Le, and M. W. Mutka. CapChain: A privacy preserving access control framework based on blockchain for pervasive environments. In Proceedings of IEEE International Conference on Smart Computing, pp. 57-64, 2018.
· [KYMM18] G. Kappos, H. Yousaf, M. Maller, and S. Meiklejohn. An empirical analysis of anonymity in zcash. In Proceedings of 27th USENIX Security Symposium, pp. 463-477, 2018.
· [FPSGW18] J. Frankle, S. Park, D. Shaar, S. Goldwasser, and D. Weitzner. Practical accountability of secret processes. In Proceedings of 27th USENIX Security Symposium, pp. 657-674, 2018.
· [KA18] K. Kluczniak, and M. H. Au. Fine-Tuning Decentralized Anonymous Payment Systems based on Arguments for Arithmetic Circuit Satisfiability. IACR Cryptology ePrint Archive, 2018.
· [LLWQL18] Z. Lu, W. Liu, Q. Wang, G. Qu, and Z. Liu. A privacy-preserving trust model based on blockchain for vanets. IEEE Access, vol. 6, pp. 45655-45664, 2018.
· [DCFZ18] T. Duong, A. Chepurnoy, L. Fan, and H. S. Zhou. Twinscoin: A cryptocurrency via proof-of-work and proof-of-stake. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, pp. 1-13, 2018.
· [HZ18] K. Hu, and Z. Zhang. Fast Lottery-Based Micropayments for Decentralized Currencies. In Australasian Conference on Information Security and Privacy, pp. 669-686, 2018.
2017
· [NYSS17] K. Naganuma, M. Yoshino, H. Sato, and T. Suzuki. Auditable zerocoin. In Proceedings of IEEE European Symposium on Security and Privacy Workshops, pp. 59-63, 2017.
· [CGLMMM17] A. Chiesa, M. Green, J. Liu, P. Miao, I. Miers, and P. Mishra. Decentralized Anonymous Micropayments. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 609-642, 2017.
· [SALY17] S. F. Sun, M. H. Au, J. K. Liu, and T. H. Yuen. RingCT 2.0: A Compact Accumulator-based (Linkable Ring Signature) Protocol for Blockchain Cryptocurrency Monero. In Proceedings of European Symposium on Research in Computer Security, pp. 456-474, 2017.
· [WGZX17] Z. Wan, Z. Guan, F. Zhuo, and H. Xian. BKI: Towards accountable and decentralized public-key infrastructure with blockchain. In Proceedings of International Conference on Security and Privacy in Communication Systems, pp. 644-658, 2017.
· [AZV17] M. Apostolaki, A. Zohar, and L. Vanbever. Hijacking bitcoin: Routing attacks on cryptocurrencies. In Proceedings of IEEE Symposium on Security and Privacy, pp. 375-392, 2017.
· [MDB17] A. Moinet, B. Darties, and J. L. Baril. Blockchain based trust & authentication for decentralized sensor networks. arXiv preprint arXiv:1706.01730, 2017.
· [LSTKKN17] X. Liang, S. Shetty, D. Tosh, C. Kamhoua, K. Kwiat, and L. Njilla. Provchain: A blockchain-based data provenance architecture in cloud environment with enhanced privacy and availability. In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, pp. 468-477, 2017.
· [KMHKB17] H. Kopp, D. Mödinger, F. Hauck, F. Kargl, and C. Bösch. Design of a privacy-preserving decentralized file storage with financial incentives. In Proceedings of IEEE European Symposium on Security and Privacy Workshops, pp. 14-22, 2017.
· [CGLMMM17] A. Chiesa, M. Green, J. Liu, P. Miao, I. Miers, and P. Mishra. Decentralized anonymous micropayments. In Proceedings of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 609-642, 2017.
· [SRKKN17] S. Shetty, V. Red, C. Kamhoua, K. Kwiat, and L. Njilla. Data provenance assurance in the cloud using blockchain. In Proceedings of SPIE 10206, Disruptive Technologies in Sensors and Sensor Systems, 102060I, 2017.
· [GM17] M. Green, and I. Miers. Bolt: Anonymous payment channels for decentralized currencies. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 473-489, 2017.
· [ACCG17] D. Augot, H. Chabanne, O. Clémot, and W. George. Transforming face-to-face identity proofing into anonymous digital identity using the bitcoin blockchain. In Proceedings of 15th Annual Conference on Privacy, Security and Trust, pp. 25-2509, 2017.
· [CGGN17] M. Campanelli, R. Gennaro, S. Goldfeder, and L. Nizzardo. Zero-knowledge contingent payments revisited: Attacks and payments for services. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, pp. 229-243, 2017.
· [XCGLS17] L. Xu, L. Chen, Z. Gao, Y. Lu, and W. Shi. CoC: secure supply chain management system based on public ledger. In Proceedings of 26th International Conference on Computer Communication and Networks, pp. 1-6, 2017.
· [HFC17] S. H. Hashemi, F. Faghri, and R. H. Campbell. Decentralized user-centric access control using pubsub over blockchain. arXiv preprint arXiv:1710.00110, 2017.
· [LOE17] H. Lycklama à Nijeholt, J. Oudejans, and Z. Erkin. Decreg: A framework for preventing double-financing using blockchain technology. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, pp. 29-34, 2017.
· [PSRK17] C. Patsonakis, K. Samari, M. Roussopoulos, and A. Kiayias. Towards a smart contract-based, decentralized, public-key infrastructure. In Proceedings of International Conference on Cryptology and Network Security, pp. 299-321, 2017.
· [KFTS17] A. Kumar, C. Fischer, S. Tople, and P. Saxena. A traceability analysis of monero’s blockchain. In Proceedings of European Symposium on Research in Computer Security, pp. 153-173, 2017.
· [FV17] G. Fanti, and P. Viswanath. Anonymity properties of the Bitcoin P2P network. arXiv preprint arXiv:1703.08761, 2017.
· [XSSAZ17] Q. Xia, E. Sifah, A. Smahi, S. Amofa, and X. Zhang. BBDS: Blockchain-based data sharing for electronic medical records in cloud environments. Information, vol. 8, no. 2, pp. 44, 2017.
· [CZJKJS17] E. Cecchetti, , F. Zhang Y. Ji, A. Kosba, A. Juels, and E. Shi. Solidus: Confidential distributed ledger transactions via PVORM. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 701-717, 2017.
2016
· [AS16] N. Z. Aitzhan, and D. Svetinovic. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 5, pp. 840-852, 2016.
2015
· [N15] S. Noether. Ring SIgnature Confidential Transactions for Monero. IACR Cryptology ePrint Archive, 1098, 2015.
· [ZGHIW15] J. H. Ziegeldorf, F. Grossmann, M. Henze, N. Inden, and K. Wehrle. Coinparty: Secure Multi-party Mixing of Bitcoins. In Proceedings of the 5th ACM Conference on Data and Application Security and Privacy, pp. 75-86, 2015.
· [VR15] L. Valenta, and B. Rowan. Blindcoin: Blinded, Accountable Mixes for Bitcoin. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 112-126, 2015.
2014
· [SCGMTV14] E. B. Sasson, A. Chiesa, C. Garman, M. Green, I. Miers, E. Tromer, and M. Virza. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of IEEE Symposium on Security and Privacy, pp. 459-474, 2014.
· [BNMCKF14] J. Bonneau, A. Narayanan, A. Miller, J. Clark, J. A. Kroll, and E. W. Felten. Mixcoin: Anonymity for Bitcoin with accountable mixes. In Proceedings of International Conference on Financial Cryptography and Data Security, pp. 486-504, 2014.
· [GCKG14] A. Gervais, S. Capkun, G. O. Karame, and D. Gruber. On the privacy provisions of bloom filters in lightweight bitcoin clients. In Proceedings of the 30th Annual Computer Security Applications Conference, pp. 326-335, 2014.
2013
· [MGR13] I. Miers, C. Garman, M. Green, and A. D. Rubin. Zerocoin: Anonymous Distributed E-cash from Bitcoin. In Proceedings of IEEE Symposium on Security and Privacy, pp. 397-411, 2013.





